The Problem: Fraud Tools Weren't Built for Here
If you're running a fintech in Lagos, Nairobi, Cairo, or Johannesburg, you already know the fraud playbook looks different:
SIM swap attacks that bypass 2FA because attackers understand local carrier porting processes
Device sharing across family members or communities that triggers false positives in Western fraud systems
Synthetic identities using stolen KYC docs that get reused across multiple accounts
VPN/proxy laundering through datacenter ASNs to mask mule network activity
Referral and bonus abuse from coordinated fraud rings using shared devices
The tools built for Stripe's fraud in San Francisco don't understand MTN's porting behavior in Kampala. They flag legitimate users for "suspicious" patterns that are actually normal in emerging markets — or worse, they miss the sophisticated local fraud happening right under their noses.
The result? You're either losing money to fraud or losing customers to friction. Often both.
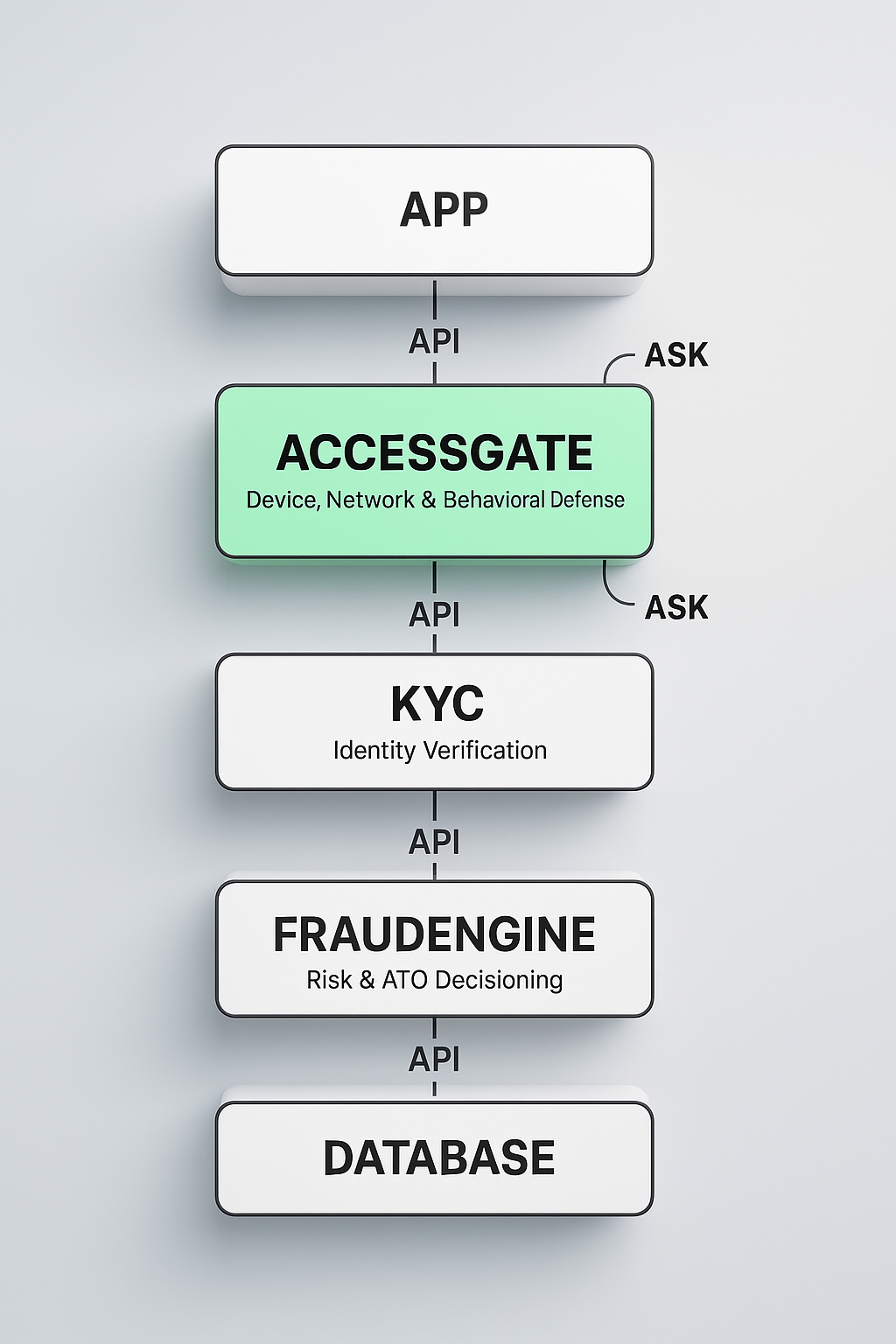
How AccessGate Works
AccessGate sits between your app and your backend as a continuous trust layer — evaluating risk at every critical checkpoint: signup, login, KYC, and payment.
Here's the flow:
1. Lightweight SDK data collection
Our browser/mobile SDK (< 25KB) runs silently in your app, collecting behavioral signals:
Mouse movement patterns (speed, curvature, hesitation)
Keystroke dynamics (typing rhythm, hold times)
Session navigation (page flow, scroll depth, time on page)
Device fingerprinting (screen resolution, timezone, installed fonts)
No performance impact. Works on 3G networks. Privacy-safe by design.
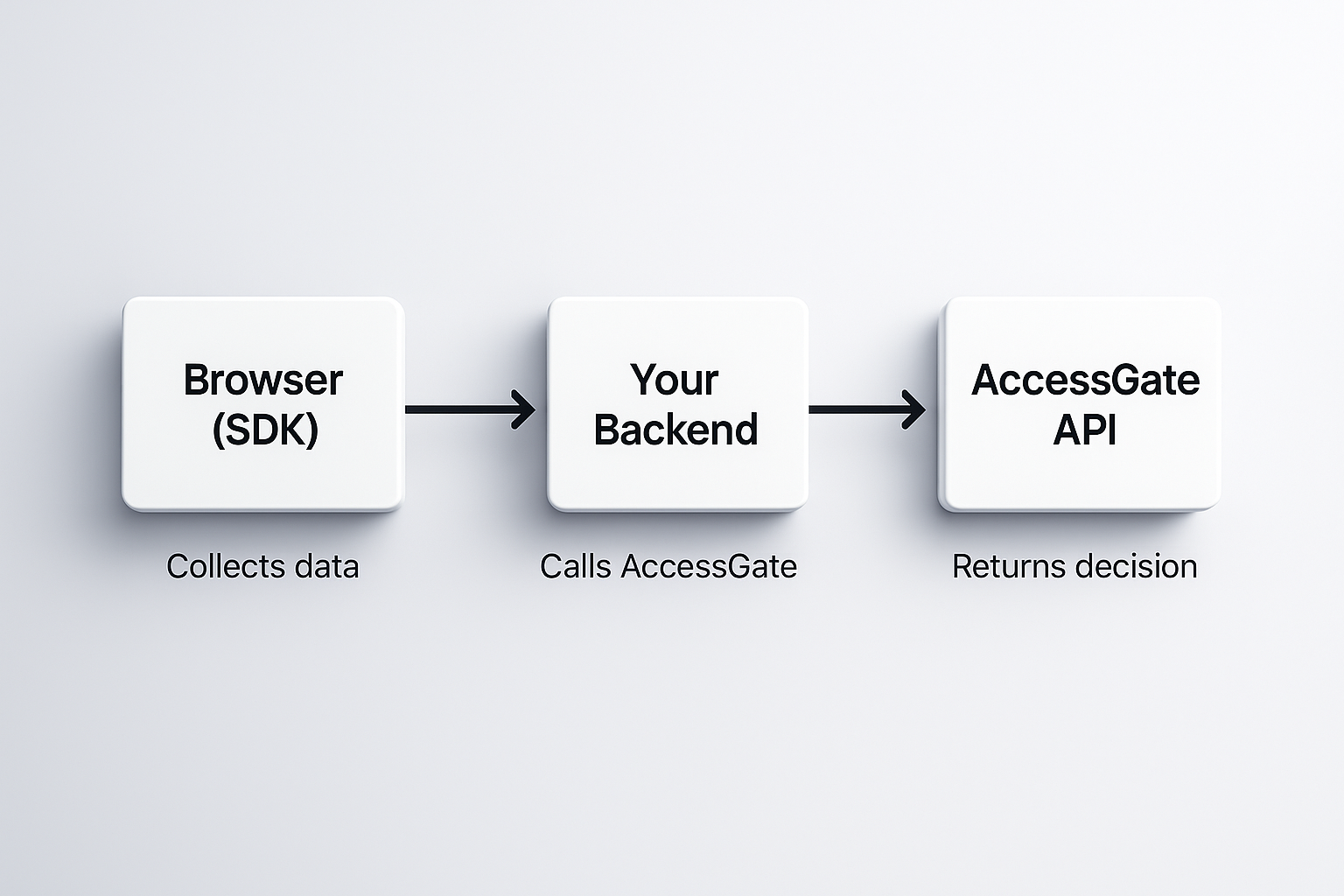
2. Your Backend Calls AccessGate
At key moments (signup, login, payment), your backend sends the SDK data plus basic identifiers (IP, email, phone) to our API
3. AccessGate Analyzes 15+ Signals in Real-Time
Our edge infrastructure (running on Cloudflare with nodes in Lagos, Nairobi, Joburg, Cape Town) processes:
Network Intelligence:
HLR lookups for SIM swap/porting detection
ASN analysis (VPN/datacenter/residential detection)
Impossible travel (location velocity checks)
Carrier risk scoring (proprietary African/GCC heuristics)
Behavioral Biometrics:
Mouse/touch pattern authenticity (human vs bot)
Keystroke dynamics baseline matching
Session flow analysis (navigation entropy)
Device & Session:
Multi-account device fingerprinting
Session correlation via ASK (Access Session Key)
Timezone/locale consistency checks
All in < 200ms.
4. You Get an Actionable Decision
You decide what to do: allow, challenge (step-up auth), or block. Full explainability. No black boxes.
What Makes AccessGate Different
Built for African Fraud Patterns
SIM swap protection via HLR + carrier porting intelligence (critical in Nigeria, Kenya, South Africa)
Device sharing intelligence that adapts to legitimate multi-user scenarios vs fraud rings
Regional carrier expertise with proprietary heuristics for MTN, Airtel, Safaricom, Etisalat/9mobile behavior
Local infrastructure optimized for 3G networks and intermittent connectivity
Continuous Trust, Not Point-in-Time Checks
Traditional fraud tools check once, at signup or payment. AccessGate uses ASK (Access Session Keys) to correlate behavior across the entire user journey:
Pre-KYC (catch bots/farms before they cost you verification fees)
Post-KYC (detect account takeovers after identity verification)
Pre-payment (stop fraud before money moves)
Every checkpoint feeds the same session identity, building a behavioral baseline that catches subtle drift (new device, IP change, typing pattern anomaly) that signals compromise.
Privacy-Safe Architecture
GDPR/NDPR compliant with built-in export and deletion endpoints
PII-minimal design: ASK tokens correlate sessions without requiring a permanent user identifier
Org isolation: Your data is siloed by org_id — no cross-client sharing
Edge-native: Data processed locally in African PoPs, not round-tripped to US servers
Built to Integrate, Not Replace
AccessGate augments your existing stack:
Works with your KYC provider (Smile ID, Youverify, Dojah, etc.)
Feeds into your fraud engine (Flagright, in-house rules, Loci Fraud AI)
Standard JSON API — plug into any decision workflow
Webhook support for real-time fraud event streaming
Private Beta: What We're Offering
We're onboarding 3-5 pilot partners to validate AccessGate in production African fintech environments.
What You Get:
✅ 5,000 MAU free for 3 months (includes bundled HLR lookup costs — normally $0.005/check)
✅ White-glove integration support (1-day setup assistance, shared Slack channel)
✅ Weekly fraud intelligence sharing (learnings from other African fintech pilots)
✅ Direct access to the engineering team (no support tickets, just Slack/email us)
✅ Dashboard analytics (fraud trends, signal performance, false positive tracking)
What We Ask:
Feedback on signal accuracy (what's working, what's not)
Integration feedback (SDK performance, API latency, edge cases)
Optional case study (if results are strong, help us tell the story)
Timeline:
Application closes: November 10th, 2025
Integration: November 12-22 (we'll help)
Pilot runs: 3 months (through February 2026)
Frequently Asked Questions
1. What exactly does AccessGate do?
AccessGate is a real-time fraud detection API built for African and GCC fintech. It analyzes 15+ signals (device fingerprinting, behavioral biometrics, HLR lookups, network patterns, impossible travel, etc.) at critical checkpoints (signup, login, payment) and returns a trust score in <200ms. You decide what to do with risky sessions—block, challenge, or allow.
2. How does it integrate with our existing stack?
Simple 3-step integration:
Install our lightweight SDK in your frontend (collects behavioral data silently)
Send collected data + basic identifiers (IP, email, phone) from your backend to our API at key checkpoints
Receive a JSON response with decision, score, reasons, and optional challenge_endpoint
Works alongside your current KYC provider (Smile ID, Youverify, etc.) or fraud engine (Flagright, in-house rules). We don't replace—we augment.
3. What's the performance impact?
Frontend SDK: <15KB bundle size, runs passively with negligible CPU/battery impact
API latency: <500ms cold start, <200ms continuous (via Cloudflare's 300+ African PoPs)
Mobile-optimized: Works on 3G networks common in African markets
4. How does pricing work after the pilot?
Pilot: Up to 5,000 MAU free for 3 months (includes bundled HLR lookup costs)
Post-pilot: Starts at $249/month upto 10,000 MAU (or up to 100k API calls), then volume-based pricing
What's included: All 15 signals (behavioral biometrics, HLR, device fingerprinting, impossible travel), dashboard analytics, API support
5. How do you handle data privacy and compliance?
GDPR/NDPR compliant: Export and deletion endpoints included
PII-minimal design: ASK (session keys) correlate behavior without requiring user IDs; you control what identifiers you send
Data residency: Runs on Cloudflare's edge with nodes in Lagos, Nairobi, Johannesburg, Cape Town
Org isolation: Your data is siloed by org_id—no cross-client data sharing
6. What makes this better than Western fraud tools?
Built for African/GCC fraud patterns:
SIM swap detection via HLR lookups (critical in Nigeria/Kenya)
Carrier intelligence with proprietary heuristics for African/GCC phone number patterns
Device sharing awareness (common in emerging markets; our baseline model adapts in 3-5 sessions)
Infrastructure cost optimized for high-volume, low-margin markets
Local performance (<200ms from African cities vs 800ms+ with US-based APIs)
7. How quickly can we see results, and what support do you provide?
Time to value: 1-day integration (SDK + API setup), 3-5 user sessions to build a behavioral baseline
Pilot support:
White-glove integration assistance
Shared fraud pattern learnings from other African fintech pilots
Direct access to the product team
Weekly check-ins during first month
Expected impact: 20-30% improvement in catching automated/synthetic fraud compared to rules-only systems (based on internal testing)
Apply for beta:
Email [email protected]
Questions? Reach out — we're here.
Further Reading: